Text
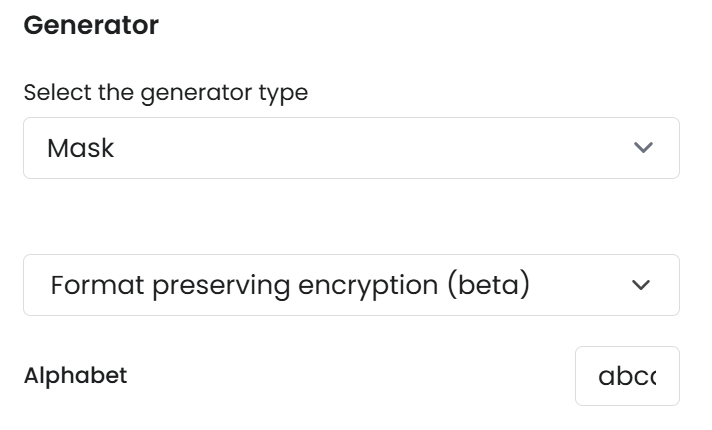
Format Preserving Encryption (FPE)
Parameters
Example
Alphabet: abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ 01234567890kVRnFWud,
uCgInrq6,
772edmb G,
...
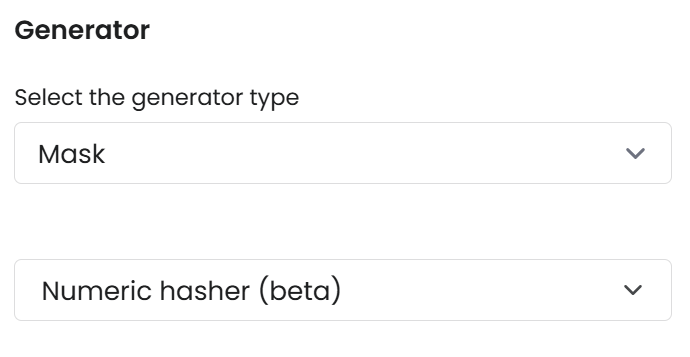
Numeric Hasher
Parameters
Example
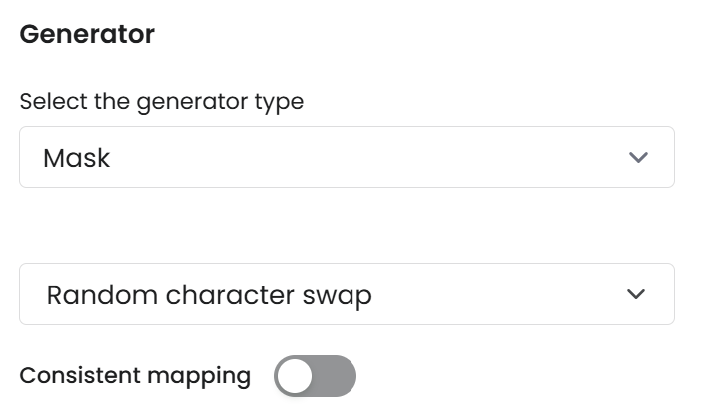
Random Character Swap
Parameters
Example
Last updated
Was this helpful?

